Decoding Rubic Exchange Exploit | QuillAudits

Summary:
On the 25th of December, 2022, Rubic Exchange suffered an exploit that led to the loss of more than $1.4 Million in users funds. Routing contracts were compromised which allowed the exploiter to steal the amount from the user's wallet who approved the router. Immediately after the hack, Rubic paused the execution of the contracts.
Introduction to Protocol and How its tech works.:
Rubic is a Cross-Chain Tech Aggregator for users and dApps. On Rubic, you can swap 15,500+ tokens across 26 blockchains. Rubic includes On-Chain & Cross-Chain swaps for Ethereum, BNB Chain, Polygon, Avalanche, Fantom, Arbitrum, Gnosis, and many more.
Check out the official docs for more info on the protocol.
Vulnerability Analysis & Impact:
On-Chain Details:
Attacker’s Contract: 0x253dD81d642220267ccAc1d8202c0B96a92b299e
Attacker’s Address: 0x001B91c794dFEecf00124D3F9525DD32870B6ee9
Rubicon Proxy: 0x3335a88bb18fd3b6824b59af62b50ce494143333
Setting USDC as Router Txn: 0x30679e7b6b410fb78368f5fb6e4c203e44d81c66ae9014c797e40856be1bbe66
Attacker transfer Txns:
0x9a97d85642f956ad7a6b852cf7bed6f9669e2c2815f3279855acf7f1328e7d46
0x6551b933b984342fd353d4b522aee7db500900e208dc1337b0c1f17647e36e56
The attack:
The cause of the hack was that the protocol added USDC tokens to their Router whitelist. Now, the router contract allowed for arbitrary calls to whitelisted addresses. And a lack of validation in the routerCallNative function allowed the hacker to drain all funds from users who have approvals to the RubicProxy.
See here: 0x30679e7b6b410fb78368f5fb6e4c203e44d81c66ae9014c797e40856be1bbe66

The attack started with the attacker funding his wallet with 0.19 ETH from the SWFT swap.

Then, the attacker took advantage of the flaw in the contract and started transferring USDC tokens from users(who approved their tokens to the router contract) to his contract via the transferFrom interface.
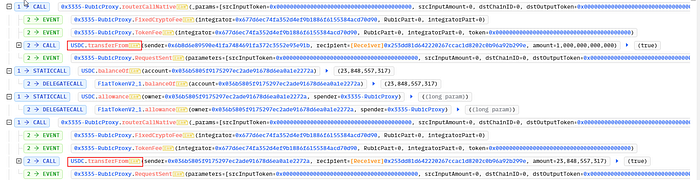
The attacker then swapped USDC tokens for ETH and sent the tokens to his wallet.

There were 2 such transactions made by hackers and around 1.45 Million were stolen by him. The hacker then transferred the stolen funds through the Tornado Cash.

After the Exploit :
Rubic Exchange announced that they have been hacked. Rubic immediately stopped all contracts to prevent further harm and asked users to remove their allowance immediately using revoke[.]cash.
Status of Funds:
The attacker immediately moved around 1188.1 ETH i.e $14.47 Million to tornado cash.

And currently, the attacker has 0.049 ETH i.e. $60 in his wallet.

Reference:
https://twitter.com/CryptoRubic/status/1606970530032230403
https://twitter.com/CryptoRubic/status/1607400412583432193

Web3 security- Need of the hour
Why QuillAudits For Web3 Security?
QuillAudits is well-equipped with tools and expertise to provide cybersecurity solutions saving the loss of millions in funds.
Want more Such Security Blogs & Reports?
Connect with QuillAudits on :
Linkedin | Twitter | Website | Newsletter | Discord | Telegram
Partner with QuillAudits :
- Affiliate program ( Refer and secure web3 )
- QuillAudits Partnership Programme ( Venture funds, launchpads, development companies, marketing firms, web2 cybersecurity firms, web3 products )
- Join Ambassdor program
